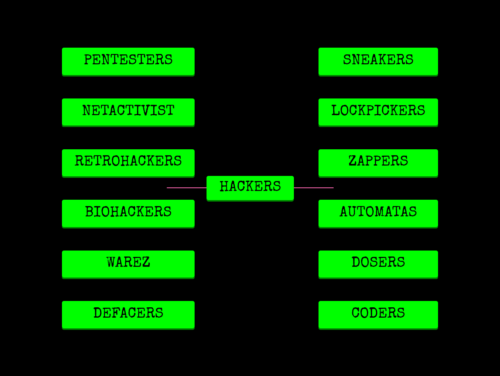
Hackers types

Hoy nos acompaña Simona Levi, una de las 25 personas que están dando forma al futuro según la revista “Rolling Stone”, para hablar de una de las características más básicas de las organizaciones: su tamaño.
Casi todos estamos de acuerdo en que la razón tras cualquier intento de organización es hacer algo, pero ¿Es inutil intentar cambiar nada sin la concurrencia de las masas como sugirieron diferentes corrientes políticas del s.XX o son los pequeños grupos decididos, insistentes y comprometidos los que cambian el mundo?
¿Qué límites impone la naturaleza, la sociedad y la cognición a la escala de nuestras organizaciones? En definitiva ¿cuantos tenemos que ser para hacer algo?
Hack_Curio is a video portal into hackerdom that helps explain why hacking is one of the most important phenomena of global culture and politics in the late 20th and early 21st century.
They are people of different kinds: they are young and old, men, women, and nonbinary. They are not invisible, immaterial, hidden or cloaked except, of course, when they want to be. Hackers are funny, and scary; hackers are do-gooders, and assholes; they write code; hunt for bugs; tell the government to fuck off; land in jail (and even break out of jail); they work for three-letter agencies and expose them; they secure and break into our systems; invent new laws; bitch and rant; whistle, hum, and rap.
We inspire women to fall in love with programming.
Django Girls organize free Python and Django workshops, create open sourced online tutorials and curate amazing first experiences with technology.
Django Girls is a non-profit organization and a community that empowers and helps women to organize free, one-day programming workshops by providing tools, resources and support. We are a volunteer run organization with hundreds of people contributing to bring more amazing women into the world of technology. We are making technology more approachable by creating resources designed with empathy.
During each of our events, 30-60 women build their first web application using HTML, CSS, Python and Django.
Amish lives are anything but anti-technological. In fact on my several visits with them, I have found them to be ingenious hackers and tinkers, the ultimate makers and do-it-yourselfers and surprisingly pro technology.
Some orders require the buggy to be an open carriage (so riders – teenagers, say – are not tempted with a private place to fool around); others will permit closed carriages. Some orders allow tractors on the farm, if the tractors have steel wheels; that way a tractor can’t be “cheated” to drive on the road like a car. Some groups allow farmers to power their combine or threshers with diesel engines, if the engine only drives the threshers but is not self-propelled, so the whole smoking, noisy contraption is pulled by horses. Some sects allow cars, if they are painted entirely black (no chrome) to ease the temptation to upgrade to the latest model.
When cars first appeared at the turn of last century the Amish noticed that drivers would leave the community to go shopping or sight-seeing in other towns, instead of shopping local and visiting friends, family or the sick on Sundays. Therefore the ban on unbridled mobility was aimed to make it hard to travel far, and to keep energy focused in the local community.
Turns out the Amish make a distinction between using something and owning it. The Old Order won’t own a pickup truck, but they will ride in one. They won’t get a license, purchase an automobile, pay insurance, and become dependent on the automobile and the industrial-car complex, but they will call a taxi.
The CCC describes itself as “a galactic community of life forms, independent of age, sex, race or societal orientation, which strives across borders for freedom of information…”. In general, the CCC advocates more transparency in government, freedom of information, and the human right to communication. Supporting the principles of the hacker ethic, the club also fights for free universal access to computers and technological infrastructure as well as the use of open-source software. The CCC spreads an entrepreneurial vision refusing capitalist control. It has been characterised as “…one of the most influential digital organisations anywhere, the centre of German digital culture, hacker culture, hacktivism, and the intersection of any discussion of democratic and digital rights”.
A Hackbase or Hackerbase is a Live-in Hackerspace – a hackerspace with a capacity for coliving.
everything you would expect from a hackerspace + place to stay (sleep, eat, …)
… this includes being publicly accessible (via a clear and non-discriminatory process)
able to host short or long-term stays
residents cover their own costs (which are usually far less than “normal” lifestyles)
extension on the practices of sharing already present in hackerspaces
hosts hacker Residencies and Exchanges
Hace unos días hemos certificado la construcción de unos juegos en un cole. Es la primera vez que esto ocurre y estamos muy contentos.
Certificar nos permite, por un lado, legitimar otro tipo de trabajo (entre lo formal y lo informal), frente a grandes empresas del sector que tienen actualmente el negocio de la homologación.
Fsociety Hacking Tools nos provee de varias herramientas destinadas para diferentes usos, entre los que encontramos:
Recopilación de información
Ataques de contraseñas
Pruebas inalámbricas
Herramientas de explotación
Sniffing y Spoofing
Piratería web
Piratería web privada
Explotación posterior
transparency for the powerful, privacy for the weak.
In a time that we’re sure that our communications are being intercepted the most dangerous consequences is auto-censorship
put in common resources and tools for care in accordance with hackers ethics and peer-to-peer philosophy
we wish to contribute to the resiliency and prosperity of what we see as an extended network of caregivers: hackers-activists, lawyers, journalists, artists, whistle-blowers, many others with or without a “profession” or a “name”, distant and near, free and imprisoned, each of us node in a human support network.