Push-button installer of macOS on VirtualBox
macos-guest-virtualbox.sh is a Bash script that creates a macOS virtual machine guest on VirtualBox with unmodified macOS installation files downloaded directly from Apple servers.
Circuit Bending Wiki
The Circuit Bending Wiki is an ongoing community project, intended to serve as a central place for circuit benders, hardware modders, and keyboard enthusiasts to share information in a way that is collaborative and easy-to-use.
Generally, if its useful to circuit benders, it belongs here.
More specifically: Personal build notes, bend points and diagrams, device documentation (like service manuals, IC info, device specs, etc.), tutorials from defunct sites & blogs…
Basically, we’re trying to compile as much practical info as we can, new and old. We’d like to use this Wiki to archive existing info, while also encouraging users to contribute their own original content, and share their findings.
Ready Player One

Ready Player One is a 2011 science fiction novel, and the debut novel of American author Ernest Cline. The story, set in a dystopia in 2045, follows protagonist Wade Watts on his search for an Easter egg in a worldwide virtual reality game
Anatomie d’une chute
“Anatomie d’une chute” revisite le film de procès – procès qui va déterminer la vérité, non seulement sur une mort, mais aussi sur un couple.
Hacking law firms with abandoned domain names
Email is an essential service in every business, and the effect of a company losing control over their email service is devastating, even if the company has merged or shut down. Sensitive information and documents are often exchanged over emails between clients, colleagues, vendors and service providers due to the convenience. Consequently, if a bad actor takes control of an entire business’s email service, sensitive information can end up in wrong hands.
What’s in My Bag, 2023
Lately, I’ve been curious about the quality of air. I carry the Aranet4 CO2 monitor to gain insight about different spaces. Higher CO2 literally makes your brain slower!
When to open a link in new tab by default?
Almost all my research online recommended that don’t make it open in a new tab. The main reasons are
1. The default behavior of hyperlinks is that they open within the same page.
2. Let the users choose it themselves.
Inside the online world of people who think they can change their race
Practitioners of “race change to another,” or RCTA, purport to be able to manifest physical changes in their appearance and even their genetics to truly become a different race.
Practitioners of what they call “race change to another,” or RCTA, purport to be able to manifest physical changes in their appearance and even their genetics to become a different race. They tune in to subliminal videos that claim can give them an “East Asian appearance” or “Korean DNA.”
Experts agree race is not genetic. But they contend that even though race is a cultural construct, it is impossible to change your race because of the systemic inequalities inherent to being born into a certain race.
David Freund, a historian of race and politics and an associate professor at the University of Maryland, College Park, corroborates the idea that a “biological race” does not exist. What we know today as “race” is a combination of inherited characteristics and cultural traditions passed down through generations, he said.
Transracial (identity)
A transracial person is one who identifies as a different race than the one associated with their biological ancestry. They may adjust their appearance to make themselves look more like that race, and may participate in activities associated with that race. Use of the word transracial to describe this is new and has been criticized, because the word was historically used to describe a person raised by adoptive parents of a different ethnic or racial background, such as a Black child adopted and raised by a White couple.
New Books Network: Against the Commons. A Radical History of Urban Planning
Characterized by shared, self-managed access to food, housing, and basic conditions for a creative life, the commons are essential for communities to flourish and protect spaces of collective autonomy from capitalist encroachment. In a narrative spanning more than three centuries, Against the Commons: A Radical History of Urban Planning (University of Minnesota Press, 2022) provides a radical counter history of urban planning that explores how capitalism and spatial politics have evolved to address this challenge. Highlighting episodes from preindustrial England, New York City and Chicago between the 1850s and the early 1900s, Weimar-era Berlin, and neoliberal Milan, Álvaro Sevilla-Buitrago shows how capitalist urbanization has eroded the egalitarian, convivial life-worlds around the commons.
In this episode, channel host Tayeba Batool talks with Dr. Álvaro Sevilla-Buitrago on the book’s argument about the ways through which urbanization shapes the social fabric of places and territories. The conversation touches upon the impact of planning and design initiatives on working-class communities and popular strata, and the various, multiple, and incremental modes of dispossession that are implicated in struggles over land, shared resources, public space, neighborhoods, creativity, and spatial imaginaries. We hear from Dr. Sevilla-Buitrago about the possibilities and alternates to a post-capitalist urban planning, one in which the structure of collective spaces is ultimately defined by the people who inhabit them.
Dr. Álvaro Sevilla-Buitrago is an Associate Professor of Urban Planning at the School of Architecture, Universidad Politécnica de Madrid. Tayeba Batool is a PhD Candidate in Anthropology at the University of Pennsylvania.
A new future for icanhazip
Lifehacker’s Australian site featured a post about icanhazip.com and traffic went through the roof. My little Slicehost instance was inundated and I quickly realized my Apache and Python setup was not going to work long term.
I migrated to nginx and set up nginx to answer the requests by itself and removed the Python scripts. The load on my small cloud instances came down quickly and I figured the issue would be resolved for a while.
Máquinas de Amor y Gracia
Lanzada con poco bombo durante los primeros días de la pandemia, la serie de ocho capítulos DEVS es una de las ficciones de los últimos años con más posibilidades de convertirse en un futuro clásico de culto. Ambientada en un Silicon Valley crepuscular profundamente melancólico, esta historia del cineasta británico Alex Garland no trata directamente sobre la inteligencia artificial: su argumento traza una fábula sobre la computación cuántica, el destino frente al libre albedrío, y la posibilidad de reconstruir cada momento único de la experiencia humana. A Jorge Luis Borges probablemente le habría entusiasmado.
La historia se ha contado mil veces. Si tuviésemos que explicar los orígenes del ideario intelectual de la industria tecnológica –de lo que Richard Barbrook y Andy Cameron llamaron “la ideología californiana”– sus componentes fundamentales son el improbable encuentro hace seis décadas al sur de San Francisco entre hippies e ingenieros informáticos; entre una visión tecnocrática heredada del complejo industrial-militar de la guerra fría, y los deseos de emancipación colectiva y liberación de la consciencia de la contracultura. El legendario Whole Earth Catalog de Stewart Brand (la publicación seminal de la cultura digital), las propuestas del visionario arquitecto Buckminster Fuller, los experimentos de convivencia planteados en comunas como Drop City… fueron caldo de cultivo para emprendedores que como Steve Jobs imaginaron un futuro cercano en que el PC era tanto un acelerador de la eficiencia como una herramienta para la realización personal y la autonomía creativa. Una prótesis intelectual, una “bicicleta de la mente” que nos permitiría llegar a donde no seríamos capaces como especie exclusivamente biológica.
La industria tecnológica se sitúa hoy en su momento más existencial desde al menos los años 90, con la emergencia de la Internet comercial. El movimiento pro ética de la IA cree que los posibles riesgos del Deep Learning y las redes neuronales requieren de un desarrollo controlado y cuidadoso que permita su introducción paulatina en todos los aspectos de la vida cotidiana. Los aceleracionistas defienden que estos miedos son conservadores y que el inevitable desarrollo de la IA traerá consigo una nueva era de prosperidad humana y crecimiento, soluciones al cambio climático y a enfermedades incurables.
…antes que una herramienta de trascendencia espiritual la IA será otro sistema de concentración de poder en un mundo en desigualdad creciente, si no cambiamos algunas de sus reglas fundamentales.
Njalla
Considered the worlds most notorious “Privacy as a Service” provider for domains, VPS’ and VPNs.
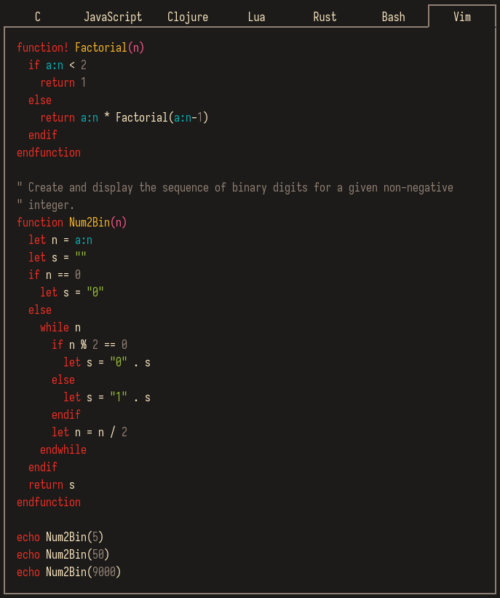
Vim: you don’t need NERDtree or (maybe) netrw
Vim’s netrw file browser is good enough. With a few tweaks there is no need for plugin like NERDtree. For many tasks you may not even need netrw.
How To Find My Public IP Address From Linux CLI
Type the following dig (domain information groper) command on a Linux, OS X, or Unix-like operating systems to see your own public IP address assigned by the ISP:
dig +short myip.opendns.com @resolver1.opendns.com
You can also type:
dig TXT +short o-o.myaddr.l.google.com @ns1.google.com
Medusa: Building blocks for digital commerce
Thousands of developers use Medusa’s open-source commerce modules and tools to build rich, reliable, and performant commerce applications without reinventing core commerce logic.
We build modularized commerce logic like carts, products, and order management and provide tools to orchestrate them for powerful ecommerce websites, POS applications, commerce-enabled products, and everything in between.
Our modules are incredibly portable and can run in modern JavaScript environments, unlocking new infrastructure for unparalleled scalability and performance, while bringing commerce enablement to new layers of your stack.
Reputation helps solve the ‘tragedy of the commons’
The problem of sustaining a public resource that everybody is free to overuse—the ‘tragedy of the commons’—emerges in many social dilemmas, such as our inability to sustain the global climate. Public goods experiments, which are used to study this type of problem, usually confirm that the collective benefit will not be produced. Because individuals and countries often participate in several social games simultaneously, the interaction of these games may provide a sophisticated way by which to maintain the public resource. Indirect reciprocity, ‘give and you shall receive’, is built on reputation and can sustain a high level of cooperation, as shown by game theorists. Here we show, through alternating rounds of public goods and indirect reciprocity games, that the need to maintain reputation for indirect reciprocity maintains contributions to the public good at an unexpectedly high level. But if rounds of indirect reciprocation are not expected, then contributions to the public good drop quickly to zero. Alternating the games leads to higher profits for all players. As reputation may be a currency that is valid in many social games, our approach could be used to test social dilemmas for their solubility.
non-extractive architecture(s)
Initiated by Space Caviar, Non-Extractive Architecture is an ongoing project aimed at collectively rethinking the balance between the built and natural landscapes, the role of technology and politics in future material economies, and the responsibility of the architect as an agent of transformation.
Srcery palette template for cmus theme
# cmus Srcery Color Scheme # Author: https://github.com/Charsinic # Directory colors set color_win_dir=7 # Normal text set color_win_fg=7 # Window background color. set color_win_bg=default # Command line color. set color_cmdline_bg=default set color_cmdline_fg=default # Color of error messages displayed on the command line. set color_error=1 # Color of informational messages displayed on the command line. set color_info=10 # Color of the separator line between windows in view (1). set color_separator=8 # Color of window titles (topmost line of the screen). set color_win_title_bg=235 set color_win_title_fg=15 # Status line color. set color_statusline_bg=235 set color_statusline_fg=15 # Color of currently playing track. set color_win_cur=10 # Color of the line displaying currently playing track. set color_titleline_bg=237 set color_titleline_fg=10 # Color of the selected row which is also the currently playing track in active window. set color_win_cur_sel_bg=237 set color_win_cur_sel_fg=10 # Color of the selected row which is also the currently playing track in inactive window. set color_win_inactive_cur_sel_bg=default set color_win_inactive_cur_sel_fg=7 # Color of selected row in active window. set color_win_sel_bg=237 set color_win_sel_fg=9 # Color of selected row in inactive window. set color_win_inactive_sel_bg=default set color_win_inactive_sel_fg=15
Srcery color palette
Srcery is dark syntax highlighting color scheme with clearly defined contrasting colors and a slightly earthy tone.
Post Type Switcher
This plugin adds a simple post-type drop-down to the post editor interface, allowing you to reassign any post to a new post type. It allows you to switch post’s type while editing your post.
Saint-Elme 3. Le Porteur de mauvaises nouvelles

Philippe Sangaré débarque à Saint-Elme et se lance sur la piste de son frère disparu. Romane révèle à Paco ce que voit réellement son père dans sa chambre. Le directeur Jansky tente une manoeuvre désespérée pour convaincre Roland Sax de signer le projet de Stan et Tania. Et sous terre, Franck se laisse guider par les grenouilles.
Saint-Elme T02. L’avenir de la famille

Franck Sangaré est aux mains des Sax, la famille qui a pris le contrôle de Saint-Elme, et son frère Philippe tarde à répondre aux appels angoissés de madame Dombre. Pendant ce temps, à l’auberge de la Vache Brûlée, Romane Mertens apprend à tirer au pistolet avec Paco tandis que son père passe ses journées à parler seul dans sa chambre… Tout seul, vraiment ?
Familias que se unen y pactan no dar móvil a sus hijos hasta los 16 años: “Así evitamos la presión social”
La idea surgió de un grupo de padres y madres a las puertas del colegio Can Manent, en Cardedeu (Barcelona). Era el curso pasado y sus hijos cursaban Sexto de Primaria. “Ellos nos iban diciendo que a fulanito ya le habían dado móvil, al otro también… Hasta que al llegar a junio la mitad de ellos ya tenía uno”, relata Rubén Terol. En muchos hogares, la reclamación de un smartphone ya generaba disputas. Hasta que este padre y otras familias, contrarias a entregar un dispositivo a sus hijos a una edad tan temprana, dieron con una solución: se juntaron en un grupo de WhatsApp y acordaron retrasar al máximo ese momento, a poder ser hasta los 16 años.
Saint-Elme 1. La Vache brûlée

Le détective Franck Sangaré, accompagné de son assistante, l’étrange madame Dombre, débarquent à Saint-Elme, une petite ville de montagne réputée pour son eau de source. Ils sont sur les traces d’un fugueur disparu depuis trois mois : enquête apparemment facile. Sauf qu’à Saint-Elme, tout le monde vous le dira : « Ici, c’est spécial. »
Avoid invisible text during font loading
font-display is an API for specifying font display strategy. swap tells the browser that text using this font should be displayed immediately using a system font. Once the custom font is ready, the system font is swapped out.
Reduce web font size
Web font optimization is a critical piece of the overall performance strategy. Each font is an additional resource, and some fonts may block rendering of the text, but just because the page is using WebFonts doesn’t mean that it has to render slower. On the contrary, optimized fonts, combined with a judicious strategy for how they are loaded and applied on the page, can help reduce the total page size and improve page rendering times.
El problema de subcontratar el pensamiento crítico
el pensamiento crítico es algo que los ciudadanos deben desarrollar individualmente, mediante una educación adecuada, la difusión de prácticas y herramientas que permitan verificar la información, y el desarrollo de hábitos saludables a la hora de informarse que defiendan la necesidad de la pluralidad de fuentes. Sustituir los libros de texto en las escuelas por procesos individuales de búsqueda y cualificación de información, desarrollar habilidades en ese sentido a lo largo de todo el curriculum educativo, y no pretender nunca que la verdad está en una sola fuente son formas de adaptarse a un entorno que, sin duda, está aquí para quedarse, y que requiere el desarrollo de nuevas habilidades.
Por contra, tratar de hacer que los ciudadanos subcontraten su pensamiento crítico a los criterios de un tercero, sea su gobierno, una plataforma social o cualquier otro organismo, es una forma de dar la batalla por perdida antes de iniciarla