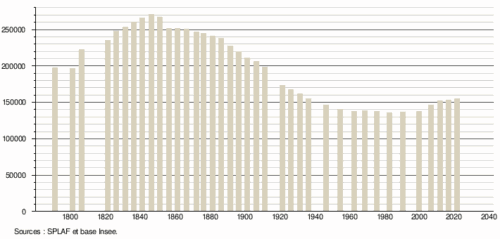
La segunda mitad del siglo XX, en pleno franquismo, fue la época de mayor construcción de vivienda en la historia de España. En solo 14 años, entre 1961 y 1975, se levantaron cuatro millones de pisos, en una operación sin precedentes. Si bien la construcción fue primero realizada por el Estado (mediante el Instituto Nacional de Vivienda), acabó, después del Plan de Estabilización de 1959 (obra del Gobierno tecnocrático formado, entre otros, por miembros del Opus Dei), siendo fiada a las grandes constructoras privadas, muchas de las cuales siguen dominando el sector.
En la posguerra, mediante el plan Bidagor, Madrid absorbe los municipios colindantes (Vallecas, Carabanchel, Chamartín, Hortaleza…) creándose el Gran Madrid. Entre 1940 y 1985 se levanta el 60% del Madrid actual. Y en 25 años la capital pasa de 800.000 habitantes a 3,2 millones, atraídos por la creciente oferta laboral en la industria y en la construcción (y a pesar de que en 1956 se promulgó una ley para impedir la llegada de extremeños, manchegos y andaluces sin dirección fija).
“Los barrios de toldo verde fueron primero ocupados por la migración interna, de otras regiones; más recientemente por la migración externa, de otros países; y ahora regresa a los barrios la gente que es expulsada de los centros urbanos, extendiendo los fenómenos de gentrificación”, explica Carbajal.
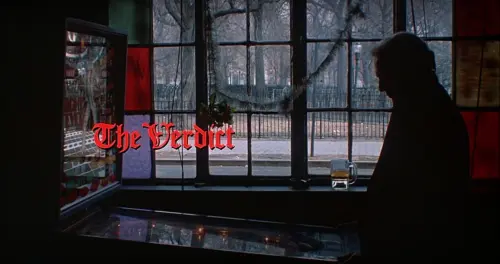
En las imágenes de Carbajal aparecen esos bares de barrio sin las ínfulas hipster del centro, bares sin adornos (no frills, como los denomina la periodista británica afincada en Lavapiés Leah Pattem), conocidos cariñosamente como bares de viejos, grasabares o bares Paco, de nombre normal y corriente como Casa Romero, El foro o La cañada. Balcones con macetas, banderas de España, camisetas tendidas, escaleras plegables, bicicletas, bombonas de butano o aparatos de aire acondicionado.
“La dictadura de Franco era un sistema corrupto y clientelar donde el régimen y los constructores se intercambiaban favores. Constructores y bancos se convierten en líderes de la economía, todavía hoy suponen un alto porcentaje del Ibex 35″. Fueron tiempos marcados por la expropiación, la recalificación, la urbanización y la especulación, sin preocupación por la calidad constructiva, lo estético o lo arquitectónico: un proceso que generó enorme riqueza para las élites urbanísticas.